The lock screen of supervised iOS devices. I use this link on open in a browser to make sure it works and opens correctly so its not a broken link.
Manage Devices With Endpoint Security In Microsoft Intune Microsoft Docs
A settings conflict occurs when a device receives two different configurations for a setting from multiple sources.

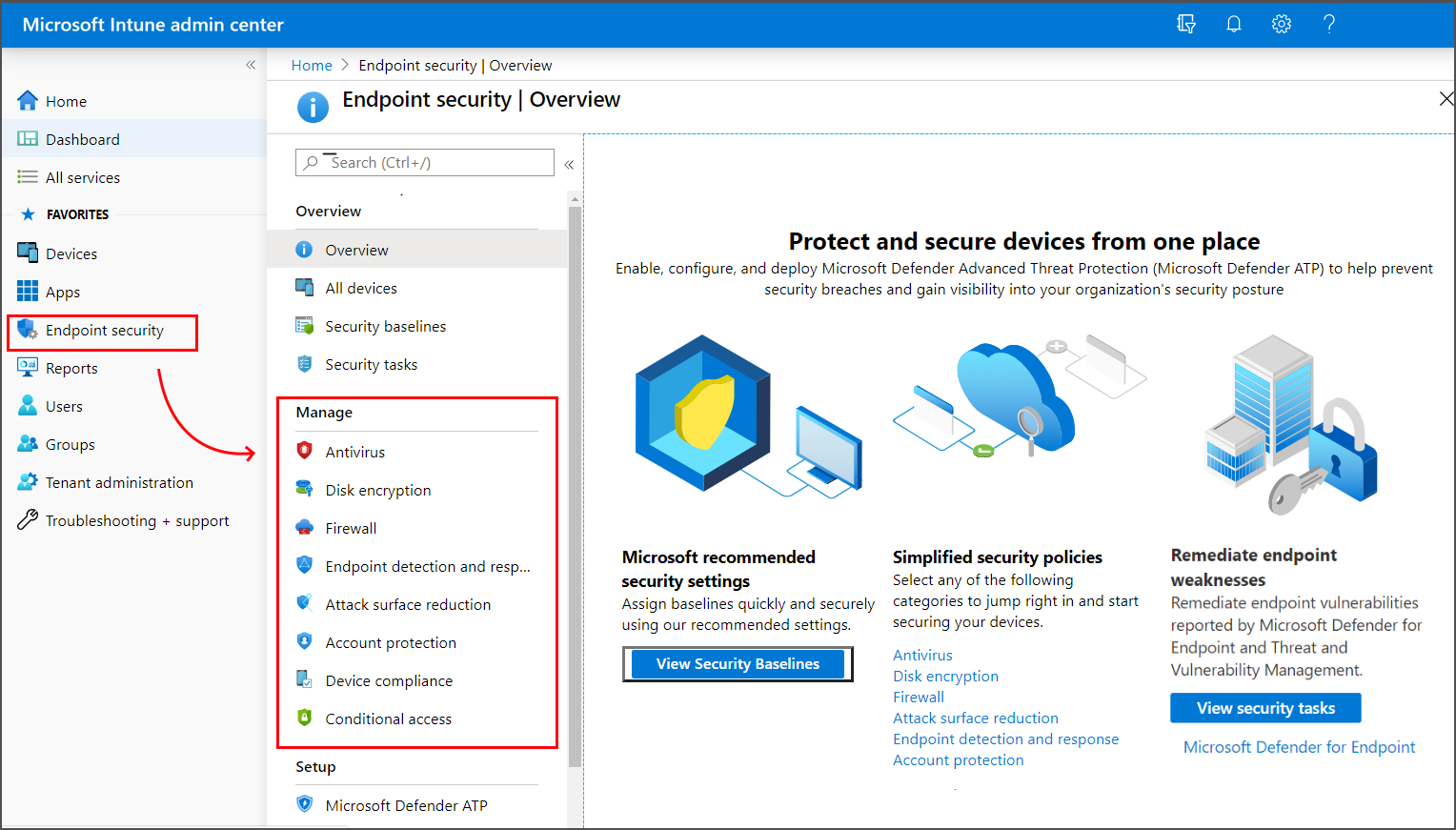
. Security baselines device configuration policies and endpoint security policies are all treated as equal sources of device configuration settings by Intune. View Device Control Removable Storage Access Control data in Microsoft Defender for Endpoint. Endpoint device control is critical to protecting organizations data assets from the risks associated with the use of removable devices.
The Microsoft 365 security portal shows removable storage blocked by the Device Control Device Installation. If you want to disable Device Control clear the Enable Device Control check. Screen locks are a form of endpoint device security control.
In the left part of the window in the Security Controls section select Device Control. The business impact analysis BIA identifies the resources for which a business continuity plan BCP is necessary. When you send a security policy such as a lock or a wipe Endpoint Management processes the policy on the device the next time the device connects.
When you connect a USB storage device or pen drive to a USB port ENS blocks it. Controls devices apps and security in one interface. In todays age of small portable storage devices the risk introduced into the network by these devices is large.
Removable Media may transfer malware to computers and can also be used to extract sensible information from computers to. Risk Threat X Vulnerability Which formula is typically used to describe the components of information security risks. Password access when not in use.
Ensure that everyone is safe. Hi all I cant seem to get the screen lock or desktop image to work through intune I use a URL which is the location of the image which I save in sharepoint. The following entry in the ENS Exploit Prevention log confirms that ENS blocked the USB storage device.
For more information see Device policies. Start studying Chapter 4. The best form of action is to be proactive and lock down any opportunity that one will download onto your computer.
This means you must avoid going to questionable sites and using an advanced scanner like Comodo Advanced Endpoint Protection to shut down lock screen ransomware before it. Do one of the following. NT AUTHORITYSYSTEM ran SystemSystem which tried to access HKLMSYSTEM.
Apple devices truncate long strings so be sure to test a string before deploying the policy to production. True Removable storage is a software application that allows an organization to monitor and control business data on a personally owned device. Set the minimum security level and complexity of screen lock codes set maximum number of failed unlock attempts set the duration after which users must change their screen lock code.
For example the administrator can. When set to Not configured Intune doesnt change or update this setting. This article describes some of the settings you can enable and configure in Windows 10 and Windows 11 devices.
In the right part of the window the settings of the Device Control component are displayed. The asset tag for the device. Screen after 2 minutes of inactivity.
At the same time these storage devices can be used to carry out sensitive data. Asset tag information for the device. Policy details are available for devices managed by MDM and Intune.
Enter the length of time a device must be idle before the screen is locked. Answer to Solved Screen locks are a form of endpoint device security. The recovery point objective RPO is the maximum amount of data loss that is acceptable.
To access the Microsoft 365 security you must have the following subscription. Remote wiping is a device security control that allows an organization to remotely erase data or email in the event of loss or theft of the device. A key lock or an equivalent control eg.
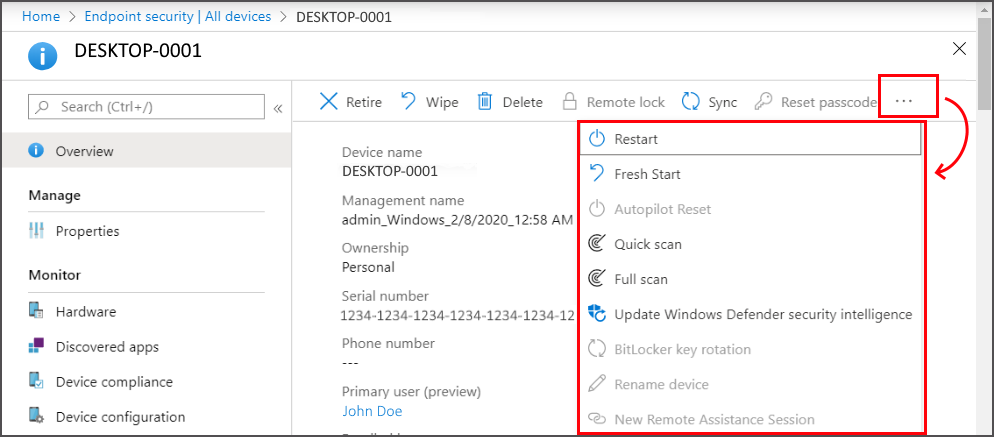
Screen locks are a form of endpoint device security control. It locks the screen after the time I put in the device configuration policy Endpoint protection Local device security options Interactive Logon Minutes of lock screen inactivity until screen saver activates Marked as answer by CloudTester Friday September 6. From the Overview page of a device you can then select Endpoint security configuration to view the endpoint security policies that apply to that device.
Endpoint Management attempts to reconnect the users device to the Endpoint Management server after a network connection loss. Endpoint and Device Security. Learn vocabulary terms and more with flashcards games and other study tools.
To add or configure this policy go to Configure Device Policies. Device Security Device security allows administrators to execute basic security policies across multiple mobile devices. Windows Explorer doesnt show the USB device and only lists the local drives.
Screen locks are a form of endpoint device security control. HIPAA 164312a The device automatically locks. Screen locks are a form of endpoint device security control.
For example enter 5 to lock devices after 5 minutes of being idle. Devices that are managed by Configuration Manager dont display policy details. Maximum minutes of inactivity until screen locks.
If you want to enable Device Control select the Enable Device Control check box. Device Control is the branch of endpoint security that refers to the control of devices access to computers. Trojans and viruses can be brought in on them defeating nearly all of the network-based anti-virus measures implemented.
Microsoft Intune includes many settings to help protect your devices. Any ideas why it doesnt display. Endpoint Management monitors the connection by transmitting.
Endpoint Security for Mobile Devices. These settings are created in an endpoint protection configuration profile in Intune to control security including BitLocker and Microsoft Defender.

Manage Devices With Endpoint Security In Microsoft Intune Microsoft Docs
Manage Endpoint Security In Microsoft Intune Microsoft Docs

What Is Endpoint Security Definition Key Components And Best Practices Toolbox It Security
0 Comments